[鹏城杯 2022]简单取证 | NSSCTF
附件是一个raw文件,一般是内存镜像用vol3看一下
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
| $ vol -f file.raw windows.info
Volatility 3 Framework 2.4.1
Progress: 100.00 PDB scanning finished
Variable Value
Kernel Base 0x804d8000
DTB 0xb37000
Symbols file:///home/wrwrw/.local/lib/python3.11/site-packages/volatility3/symbols/windows/ntkrnlpa.pdb/30B5FB31AE7E4ACAABA750AA241FF331-1.json.xz
Is64Bit False
IsPAE True
layer_name 0 WindowsIntelPAE
memory_layer 1 FileLayer
KdDebuggerDataBlock 0x80546ae0
NTBuildLab 2600.xpsp.080413-2111
CSDVersion 3
KdVersionBlock 0x80546ab8
Major/Minor 15.2600
MachineType 332
KeNumberProcessors 1
SystemTime 2022-06-20 13:00:12
NtSystemRoot C:\WINDOWS
NtProductType NtProductWinNt
NtMajorVersion 5
NtMinorVersion 1
PE MajorOperatingSystemVersion 5
PE MinorOperatingSystemVersion 1
PE Machine 332
PE TimeDateStamp Sun Apr 13 18:31:06 2008
|
是windows xp系统的,中文版的桌面叫做“桌面”而不是“Desktop”,直接搜索对应的文件
1
2
3
4
5
6
7
8
9
| $ vol -f file.raw windows.filescan |grep 桌面
0x2072ea0 100.0\Documents and Settings\Administrator\桌面\51763-4FE71AEA7-20220620-130010.raw 112
0x20dd608 \Documents and Settings\Administrator\桌面\DumpIt.exe 112
0x2162df8 \Documents and Settings\Administrator\桌面 112
0x224e028 \Documents and Settings\Administrator\桌面 112
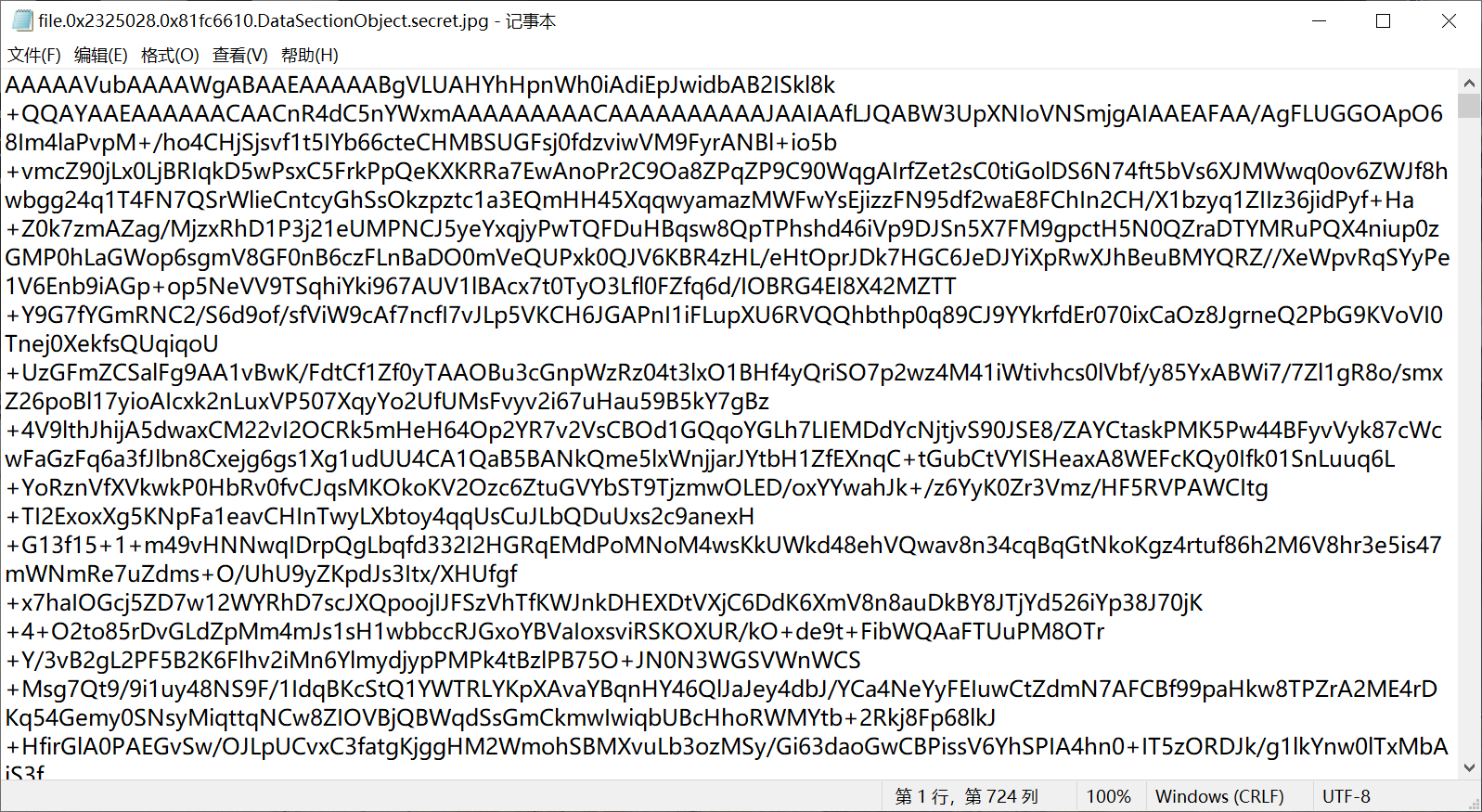
0x2325028 \Documents and Settings\Administrator\桌面\secret.jpg 112
0x23ac178 \Documents and Settings\Administrator\桌面 112
0x23d5960 \Documents and Settings\Administrator\桌面\DumpIt.exe 112
0x240d8d8 \Documents and Settings\All Users\桌面 112
|
有个secret.jpg,dump下来
1
| $ vol -f file.raw windows.dump --physaddr 0x2325028
|
发现该文件其实是base64文本的文本文件

解码后发现PK字样,猜测是压缩包直接用脚本解压后发现无法解压,用010editor打开,发现50 4b 03 04在最后面而且是反过来的,更改脚本进行反序输出
1
2
3
4
5
6
7
| from base64 import*
with open(r"file.0x2325028.0x81fc6610.DataSectionObject.secret.jpg","rb")as f:
arr=f.read()
arr=b64decode(arr)[::-1]
with open(r"a.zip","wb") as g:
g.write(arr)
|
成功输出zip,但发现有密码
对raw文件用strings搜索相应字符串,发现一个疑似密码的字段
1
2
3
4
| $ strings file.raw |grep password
#以上省略
echo password = 62b041223bb9a
#以下省略
|
解压后是一个文本,都是以数对形式存在,猜测是坐标,用于打印像素,且该文本的末尾是349 349 猜测是350*350的图片

脚本如下
1
2
3
4
5
6
7
8
9
10
11
12
| from PIL import Image
with open(r"a~\flag.txt") as f:
pixels=f.read().splitlines()
width = 350
height = 350
result=[]
img = Image.new('RGB', (width, height))
for i in pixels:
tmp=i.split(' ')
img.putpixel((int(tmp[0]),int(tmp[1])),(255,255,255))
img.save(r'a~\output.png')
|
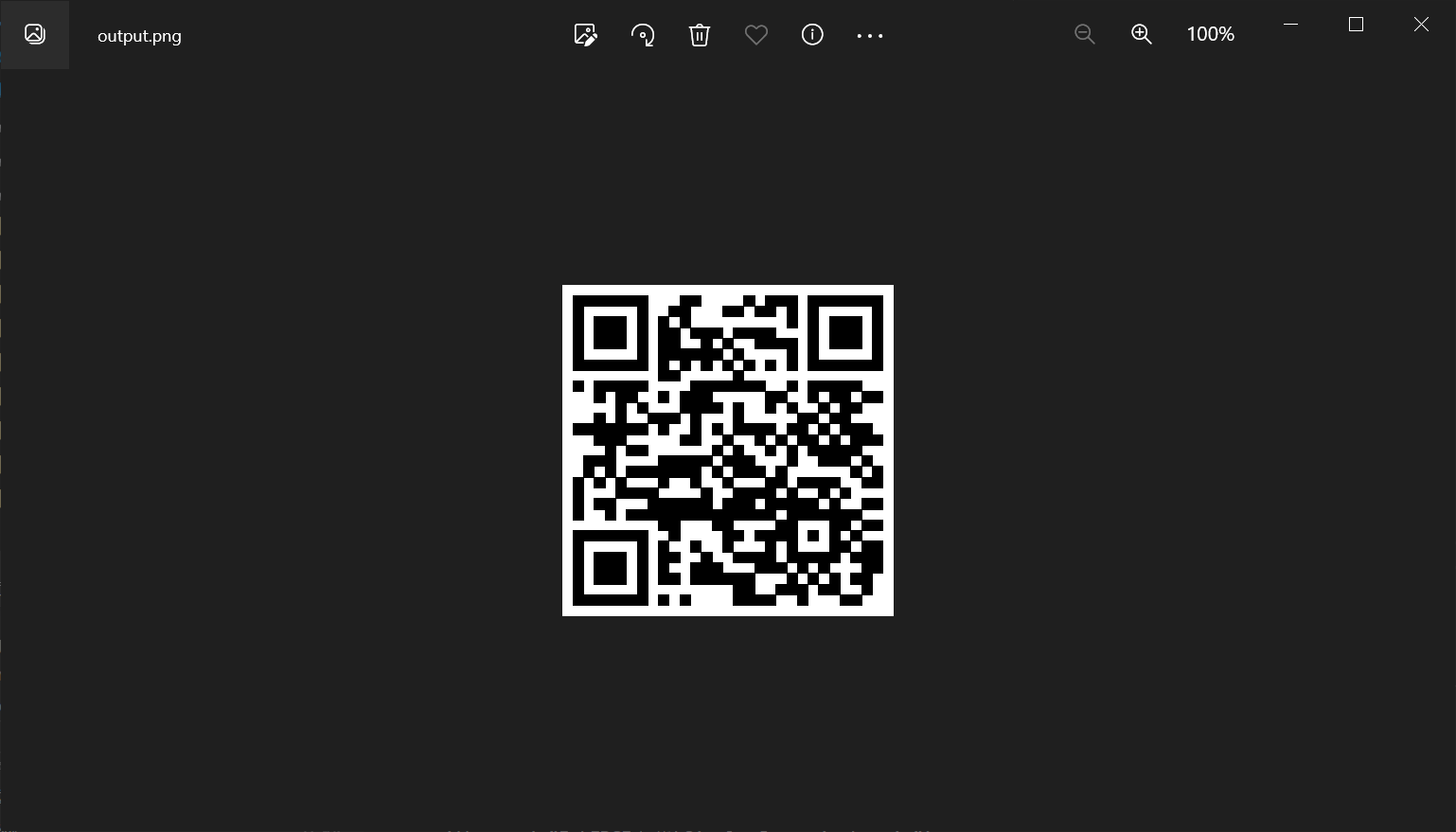
成功输出png,是一个二维码

扫描后得到了flag