[巅峰极客 2022]easy_Forensic | NSSCTF
只是个初学vol3的小草稿
附件是个raw文件(不是图片,相当于一个内存镜像)
使用volatility3进行分析
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 vol -f secret.raw windows.info Volatility 3 Framework 2.4.1 Progress: 100.00 PDB scanning finished Variable Value Kernel Base 0xf80003e06000 DTB 0x187000 Symbols file:///home/wrwrw/.local/lib/python3.11/site-packages/volatility3/symbols/windows/ntkrnlmp.pdb/F8E2A8B5C9B74BF4A6E4A48F18009994-2.json.xz Is64Bit True IsPAE False layer_name 0 WindowsIntel32e memory_layer 1 FileLayer KdDebuggerDataBlock 0xf80003fef070 NTBuildLab 7600.16385.amd64fre.win7_rtm.090 CSDVersion 0 KdVersionBlock 0xf80003fef030 Major/Minor 15.7600 MachineType 34404 KeNumberProcessors 1 SystemTime 2022-08-13 11:48:11 NtSystemRoot C:\Windows NtProductType NtProductWinNt NtMajorVersion 6 NtMinorVersion 1 PE MajorOperatingSystemVersion 6 PE MinorOperatingSystemVersion 1 PE Machine 34404 PE TimeDateStamp Mon Jul 13 23:40:48 2009
查看进程
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 vol -f secret.raw windows.pslist Volatility 3 Framework 2.4.1 Progress: 100.00 PDB scanning finished PID PPID ImageFileName Offset(V) Threads Handles SessionId Wow64 CreateTime ExitTime File output 4 0 System 0xfa8018d4b9e0 68 442 N/A False 2022-08-13 11:46:15.000000 N/A Disabled 224 4 smss.exe 0xfa80265f99f0 2 29 N/A False 2022-08-13 11:46:15.000000 N/A Disabled 300 288 csrss.exe 0xfa801ab36b30 8 342 0 False 2022-08-13 11:46:15.000000 N/A Disabled 348 288 wininit.exe 0xfa8024e80340 3 76 0 False 2022-08-13 11:46:15.000000 N/A Disabled 356 340 csrss.exe 0xfa8018e127c0 7 219 1 False 2022-08-13 11:46:15.000000 N/A Disabled 396 340 winlogon.exe 0xfa8019fa5060 6 118 1 False 2022-08-13 11:46:15.000000 N/A Disabled 440 348 services.exe 0xfa801ab2ab30 10 174 0 False 2022-08-13 11:46:15.000000 N/A Disabled 448 348 lsass.exe 0xfa801abc7060 6 511 0 False 2022-08-13 11:46:15.000000 N/A Disabled 456 348 lsm.exe 0xfa801a482910 10 138 0 False 2022-08-13 11:46:15.000000 N/A Disabled 560 440 svchost.exe 0xfa801ac4c7c0 11 352 0 False 2022-08-13 11:46:15.000000 N/A Disabled 624 440 svchost.exe 0xfa8020ba1790 7 231 0 False 2022-08-13 11:46:15.000000 N/A Disabled 676 440 svchost.exe 0xfa801ac8eb30 20 379 0 False 2022-08-13 11:46:15.000000 N/A Disabled 768 440 svchost.exe 0xfa801acbb290 22 450 0 False 2022-08-13 11:46:15.000000 N/A Disabled 844 440 svchost.exe 0xfa801acccb30 48 838 0 False 2022-08-13 11:46:15.000000 N/A Disabled 912 676 audiodg.exe 0xfa801ad22b30 7 129 0 False 2022-08-13 11:46:15.000000 N/A Disabled 1000 440 svchost.exe 0xfa801ad512f0 13 266 0 False 2022-08-13 11:46:16.000000 N/A Disabled 304 440 svchost.exe 0xfa801ad66b30 17 369 0 False 2022-08-13 11:46:16.000000 N/A Disabled 360 440 spoolsv.exe 0xfa801adfe780 13 265 0 False 2022-08-13 11:46:16.000000 N/A Disabled 1064 440 svchost.exe 0xfa801ae54b30 22 305 0 False 2022-08-13 11:46:16.000000 N/A Disabled 1236 440 taskhost.exe 0xfa801aeae140 11 204 1 False 2022-08-13 11:46:16.000000 N/A Disabled 1324 768 dwm.exe 0xfa801af42670 5 71 1 False 2022-08-13 11:46:16.000000 N/A Disabled 1336 1312 explorer.exe 0xfa801af46b30 31 724 1 False 2022-08-13 11:46:16.000000 N/A Disabled #此处有个文件资源管理器的进程 1392 440 QQProtect.exe 0xfa801af79060 15 196 0 True 2022-08-13 11:46:16.000000 N/A Disabled 1108 440 SearchIndexer. 0xfa801ae22b30 13 639 0 False 2022-08-13 11:46:22.000000 N/A Disabled 1452 1108 SearchProtocol 0xfa801af01b30 7 310 0 False 2022-08-13 11:46:22.000000 N/A Disabled 1616 1108 SearchFilterHo 0xfa801aefab30 6 93 0 False 2022-08-13 11:46:22.000000 N/A Disabled 828 1336 MRCv120.exe 0xfa801abf8060 14 282 1 True 2022-08-13 11:48:02.000000 N/A Disabled
搜索桌面文件
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 vol -f secret.raw windows.filescan |grep Desktop 0x6c9c6290 100.0\Users\Admin\Links\Desktop.lnk 216 0x6d526f20 \Users\Admin\Desktop\MRCv120.exe 216 0x72e8bf20 \Users\Admin\Desktop\EULAaccepted.dat 216 0x7d80a7d0 \Users\Admin\Desktop\gift.jpg 216#这三个文件比较重要 0x7d84af20 \Users\Admin\Desktop\hint.txt 216# 0x7d84e350 \Users\Admin\Desktop\secret.zip 216# 0x7da64360 \ProgramData\Microsoft\Windows\Start Menu\Programs\Accessories\Desktop.ini 216 0x7da66c70 \Users\Public\Desktop\desktop.ini 216 0x7da66dc0 \Users\Admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Accessories\Desktop.ini 216 0x7da68070 \Users\Admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Maintenance\Desktop.ini 216 0x7da68c00 \Users\Admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Accessories\Accessibility\Desktop.ini 216 0x7da6af20 \Users\Admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Accessories\System Tools\Desktop.ini 216 0x7da6dab0 \ProgramData\Microsoft\Windows\Start Menu\Programs\Maintenance\Desktop.ini 216 0x7da6fab0 \ProgramData\Microsoft\Windows\Start Menu\Programs\Accessories\Accessibility\Desktop.ini 216 0x7da6fc00 \ProgramData\Microsoft\Windows\Start Menu\Programs\Accessories\System Tools\Desktop.ini 216 0x7da704a0 \ProgramData\Microsoft\Windows\Start Menu\Programs\Accessories\Tablet PC\Desktop.ini 216 0x7da7f310 \Users\Admin\Desktop 216 0x7da7f4e0 \Users\Admin\Desktop 216 0x7da80740 \Users\Public\Desktop\Glary Tracks Eraser.lnk 216 0x7da81670 \Users\Public\Desktop 216 0x7da81b70 \Users\Public\Desktop 216 0x7dae0420 \Users\Admin\Desktop\wechat.txt 216 0x7dc47bc0 \ProgramData\Microsoft\Windows\Start Menu\Programs\Accessories\Remote Desktop Connection.lnk 216 0x7de7c070 \Users\Admin\Desktop\MRCv120.exe 216 0x7dfa9150 \Users\Admin\Desktop\MRCC206.tmp 216 0x7e144d20 \Users\Admin\Desktop\desktop.ini 216 0x7e614420 \Users\Admin\Desktop 216 0x7ee47230 \Users\Public\Desktop\Firefox.lnk 216 0x7f1e6ad0 \Users\Admin\Desktop\111.raw 216
dump三个文件,发现hint.txt无法dump
1 2 3 vol -f secret.raw windows.dump --physaddr 0x7d80a7d0 vol -f secret.raw windows.dump --physaddr 0x7d84af20 vol -f secret.raw windows.dump --physaddr 0x7d84e350
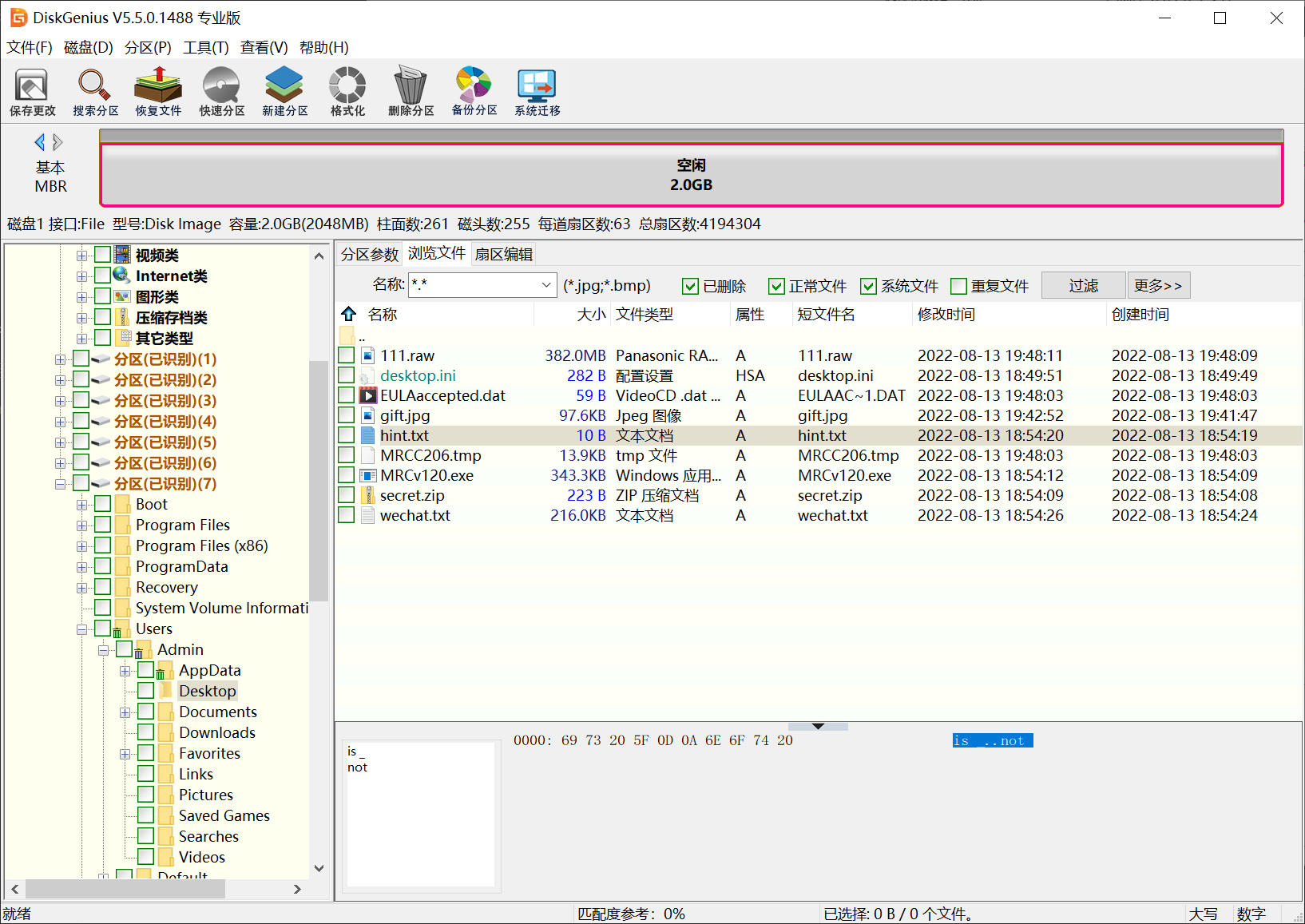
通过diskgenius打开该镜像获取文件
成功找到桌面文件
hint.txt为is _ not (此处有个空格16进制数为0x20)
其余两个文件为一个压缩包和一个jpg
jpg明显左下角有字,更改长宽
显示Nothing is more important than your life!是Passwd
输入压缩包后错误,根据hint文件中的提示,将空格转化为_
1 2 In [2 ]: "Nothing is more important than your life!" .replace(' ' ,'_' ) Out[2 ]: 'Nothing_is_more_important_than_your_life!'
解压后文件显示
1 A gift for You: wHeMscYvTluyRvjf5d7AEX5K4VlZeU2IiGpKLFzek1Q=
通过搜索wp发现是wechat数据库加密的key
wechat.txt就是被加密的数据库,直接通过diskgenius无法正常提取,通过Volatility dump下来(需要将.dat文件改成.db文件)
1 2 3 4 5 6 7 8 9 $ vol -f secret.raw windows.filescan |grep wechat 0x7dae0420 100.0\Users\Admin\Desktop\wechat.txt 216 $ vol -f secret.raw windows.dump --physaddr 0x7dae0420 Volatility 3 Framework 2.4.1 Progress: 100.00 PDB scanning finished Cache FileObject FileName Result DataSectionObject 0x7dae0420 wechat.txt file.0x7dae0420.0xfa8019afc6c0.DataSectionObject.wechat.txt.dat
然后通过搜索wechat解密脚本2022巅峰极客初赛 Misc wp - zysgmzb - 博客园 (cnblogs.com)
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 from Crypto.Cipher import AESimport hashlib, hmac, ctypesfrom base64 import *SQLITE_FILE_HEADER = bytes ("SQLite format 3" ,encoding='ASCII' ) + bytes (1 ) IV_SIZE = 16 HMAC_SHA1_SIZE = 20 KEY_SIZE = 32 DEFAULT_PAGESIZE = 4096 DEFAULT_ITER = 64000 password = b64decode(b"wHeMscYvTluyRvjf5d7AEX5K4VlZeU2IiGpKLFzek1Q=" ) with open (r'dump下来的db文件地址' , 'rb' ) as f: blist = f.read() print (len (blist))salt = blist[:16 ] key = hashlib.pbkdf2_hmac('sha1' , password, salt, DEFAULT_ITER, KEY_SIZE) first = blist[16 :DEFAULT_PAGESIZE] mac_salt = bytes ([x^0x3a for x in salt]) mac_key = hashlib.pbkdf2_hmac('sha1' , key, mac_salt, 2 , KEY_SIZE) hash_mac = hmac.new(mac_key ,digestmod = 'sha1' ) hash_mac.update(first[:-32 ]) hash_mac.update(bytes (ctypes.c_int(1 ))) if (hash_mac.digest() == first[-32 :-12 ]): print ('Correct Password' ) else : raise RuntimeError('Wrong Password' ) blist = [blist[i:i+DEFAULT_PAGESIZE] for i in range (DEFAULT_PAGESIZE,len (blist),DEFAULT_PAGESIZE)] with open (r'输出的db文件地址' , 'wb' ) as f: f.write(SQLITE_FILE_HEADER) t = AES.new(key ,AES.MODE_CBC ,first[-48 :-32 ]) f.write(t.decrypt(first[:-48 ])) f.write(first[-48 :]) for i in blist: t = AES.new(key ,AES.MODE_CBC ,i[-48 :-32 ]) f.write(t.decrypt(i[:-48 ])) f.write(i[-48 :])
成功输出
直接搜一下flag
1 2 strings a.db |grep flag klllflag{The_Is_Y0ur_prize}