广东强网杯 2021 个人决赛findthekey
只有一个activity组件
1 | package com.ctf.findthekey; |
直接调用JNI进行明文校验
发现JNI中的所有函数都不符合对应的findthekey这个名字经过搜索发现是经过了混淆(41条消息) Android SO文件保护加固——混淆篇(一)_android so 混淆_不知世事的博客-CSDN博客
需要看JNI_ONLoad(在loadlibrary时调用,用于注册函数之类的)
以下的byte_5120,byte_510C,byte_5140都在initarray时进行了修改(initarray在启动elf时就执行会先于JNI_OnLoad)
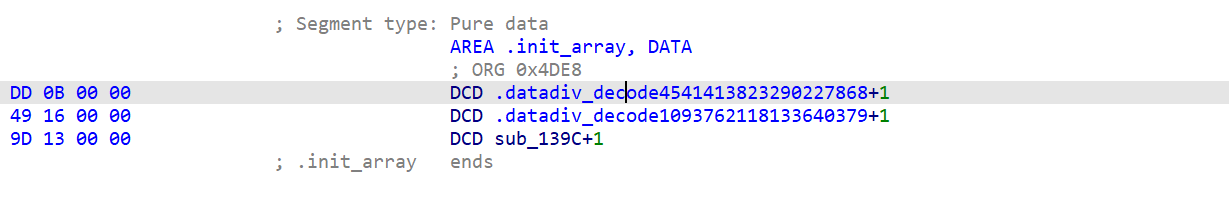
1 | jint JNI_OnLoad(JavaVM *vm, void *reserved) |
用脚本重新异或回去得出
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
for i in range(size):
idaapi.patch_byte(addr+i,Byte(addr+i)^xor)
patch(0x5004,0x20,4)
patch(0x5010,0x90,0x14)
patch(0x5025,0x54, 0xF)
patch(0x5035,0xF9,5)
patch(0x5040,0x5F,0x18)
patch(0x5060,0x6D,0x19)
patch(0x507A,0xF1,4)
patch(0x5080,0xA7,0x15)
patch(0x50A0,0x78,0x40)
patch(0x50F0,0x86,0x18)
patch(0x5109,0xF4,2)
patch(0x510C,0x74, 0xA)
patch(0x5120,0xFC,0x15)
patch(0x5140, 0x45,0x1F)
1 | jint JNI_OnLoad(JavaVM *vm, void *reserved) |
所以直接查看sub_1434函数(此处将)
1 | bool __fastcall sub_1434(int a1, int a2, int a3) |
又调用了sub_13B0
1 | bool __fastcall sub_13B0(const char *a1) |
此处的sub_1214使用的是base64算法可以通过其中的一部分代码判断(每次取三字节,生成四字节)
1 | v6[v5] = byte_50A0[*(unsigned __int8 *)(a1 + v4) >> 2]; |
根据 strcmp((_BYTE *)dword_5164, v1) == 0;可以得出dword_5164为base64后的密文
调查交叉引用,也被initarray的函数修改了
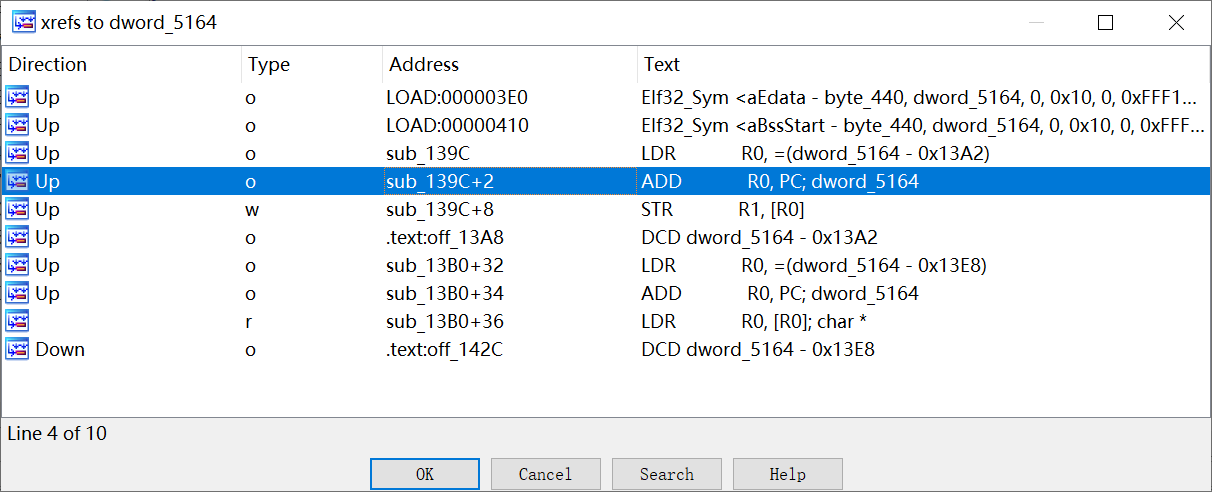
实际值为zMXHz3T0AgLZAxn0AgvRzxL9
换表后得出了flag
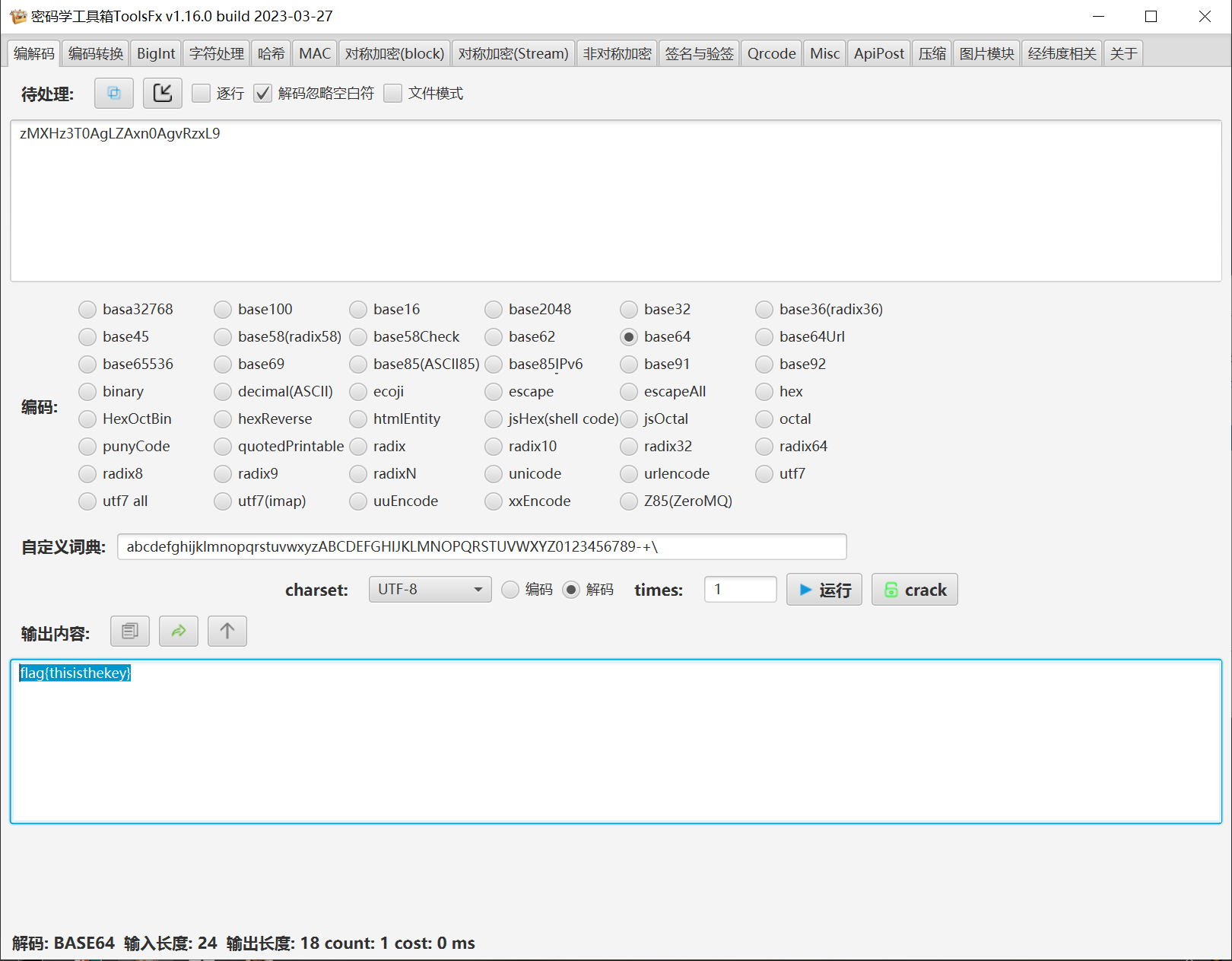
flag{thisisthekey}
- 标题: 广东强网杯 2021 个人决赛findthekey
- 作者: runwu2204
- 创建于 : 2023-07-05 11:43:17
- 更新于 : 2024-04-12 17:25:45
- 链接: https://runwu2204.github.io/2023/07/05/CTF WP/Re/安卓/广东强网杯 2021 个人决赛findthekey/
- 版权声明: 本文章采用 CC BY-NC-SA 4.0 进行许可。
评论