CISCN 2021初赛glass
查看组件,就一个activity,直接看
1 |
|
是一个标准的调用JNI接口的校验
1 | package com.ciscn.glass; |
JNI中的checkFlag函数
1 | bool __fastcall Java_com_ciscn_glass_MainActivity_checkFlag(int a1, int a2, int a3) |
写了个python脚本用于求解混淆前的rc4密文
1 | from z3 import * |
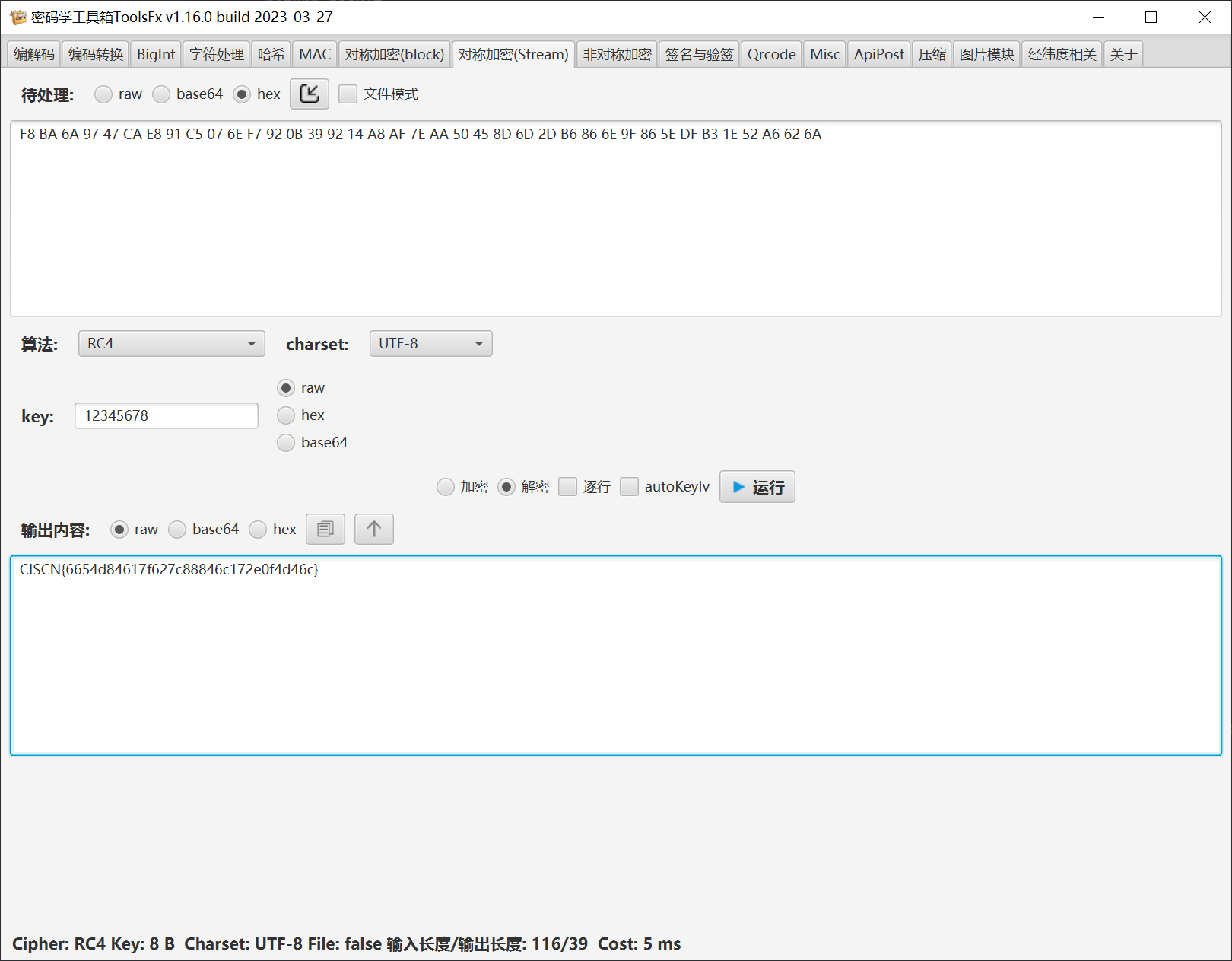
直接拿去rc4解密就行,key是12345678
- 标题: CISCN 2021初赛glass
- 作者: runwu2204
- 创建于 : 2023-06-17 00:48:51
- 更新于 : 2023-06-17 00:57:44
- 链接: https://runwu2204.github.io/2023/06/17/CTF WP/Re/安卓/CISCN 2021初赛glass/
- 版权声明: 本文章采用 CC BY-NC-SA 4.0 进行许可。
评论